
Certificate Wizard
A growing trend has been that people have become more aware about the security aspects of exposing systems to the internet. NetPhantom already today provides functionality to protect all communication through strong encryption.
Technically this means that NetPhantom implements Secure Socket Layer (SSL). Communication based on this technology encrypts communication with the help of keys. These keys are protected by digital certificates. In order for these certificates to be universally recognized, they are often issued by certificate authorities (CA). DigiCert, Symantec, GeoTrust and Thawte are examples of recognized certificate authorities.
There are a number of different formats the certificates can be stored and transferred in. In addition, the different authorities use different processes when certificates are requested, created and delivered. All this contributes to making the handling of the certificate less than trivial. To facilitate this process and to help keep the certificates safe, NetPhantom provides a Certificate Wizard.
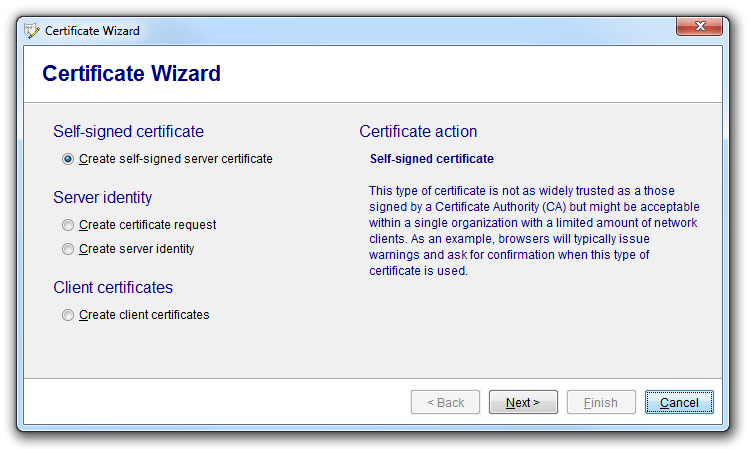
The wizard allows the means to create certificate directly (internal authentication) and to have certificates created and signed by certificate authorities (external authentication).
Self-signed certificate
A certificate which is "self-signed" (authenticated unilaterally) cannot be used to verify the other party in the communication. For example, a browser connecting to a website protected with SSL using a self-signed certificate will issue a warning for this reason. This might be sufficient is an environment with only trusted nodes are present (as in an intranet). Please note: The level of encryption of the digital communication is not affected by the use of this type of certificate - it affects only the authentication of the opposite party.
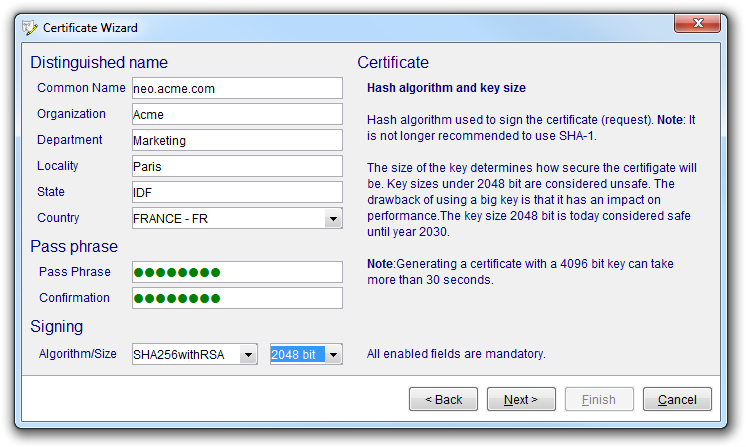
To create a self-signed certificate, three things are needed: geographical/logical identification, password to protect the certificate/key and key specification. The latter consists of the size of the key (bigger is more secure but slower) and the algorithm to use when signing.
Once the certificate is created, it can be used as a server identity (server authentication) or as a client certificate (client authentication) with the limitations described above.
Server identity
The CA signed server identity is created in two steps: Creation of a certificate request and the creation of a certificate based on the response from the certificate authority. The wizard will assist in both these steps.
The basis of the certificate request is the same as of the self-signed certificate: geographical/logical identification and the signing key (the password is defined later). The wizard will create the certificate request and the private key (stored in the SSL repository).
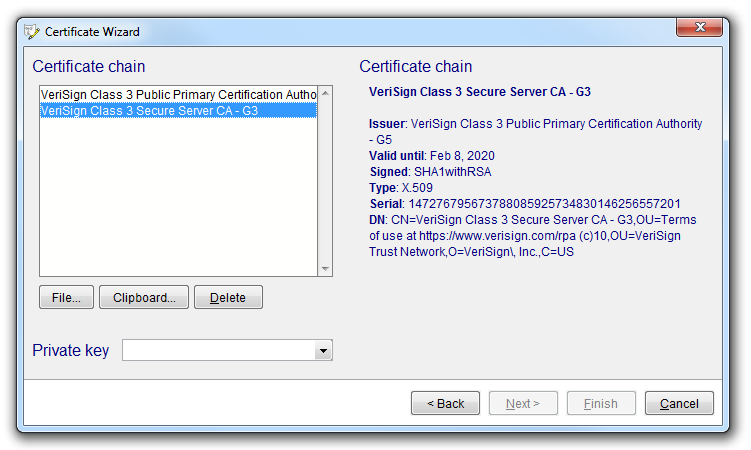
When the certificate is returned from the certificate authority, it is imported into the tool. The wizard supports a number of certificate formats and encodings which correspond to the set of currently used by the major certificate authorities. Once this is done, the list can be edited (if needed) and a private key can be chosen from the set stored in the SSL repository.
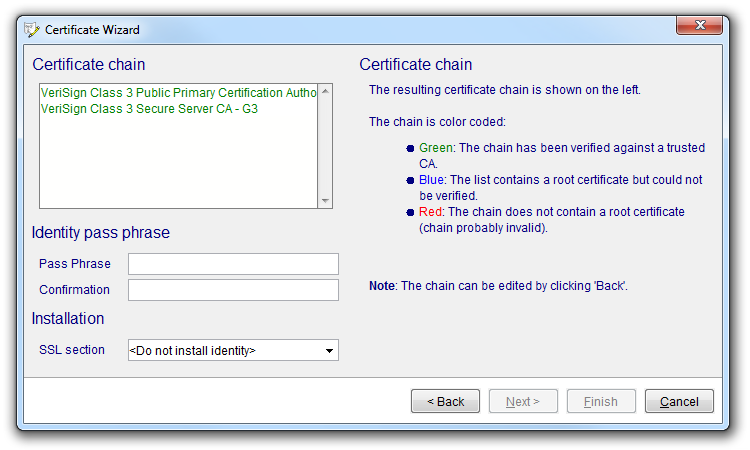
In the next stage, the certificate chain is evaluated. The chain is an ordered list of certificates, each signing the previous, ending in the certificate which was requested from the authority. The certificate chain is then signed (using a supplied password). This way and put in a container ready to be used to identify the server. The installation of the identity in the NetPhantom server can (optionally) be done by the wizard.
Client certificates
The certificates used authenticating clients can be created in batch mode, making the process a lot smoother if many clients are to be handled. These certificates are used by the server to allow/prevent access by the authenticated client.
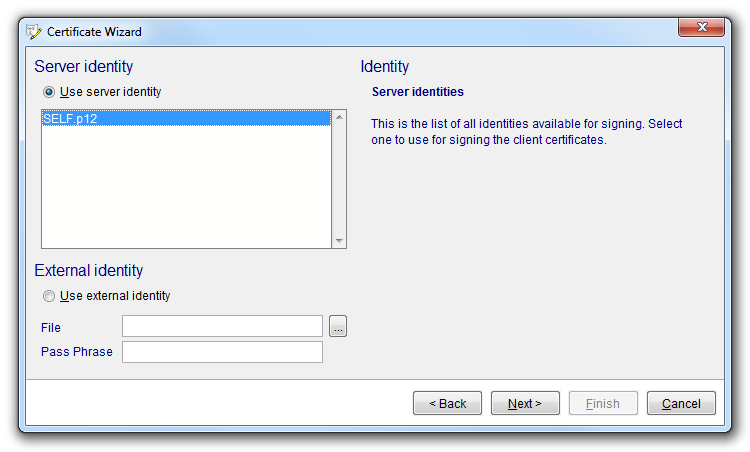
The client certificates can be signed by the current server identity or by an external identity (certificate). Signing of the server identity is a streamlined way of establishing the identity of connected clients. The client certificates can be signed by the server certificate and installed directly. After that, very little further configuration is needed. If an external identity is used, the corresponding certificates must be specifically made known to the server.
In the next step, the list of clients is compiled, each identified by the geographical/logical information we saw earlier.
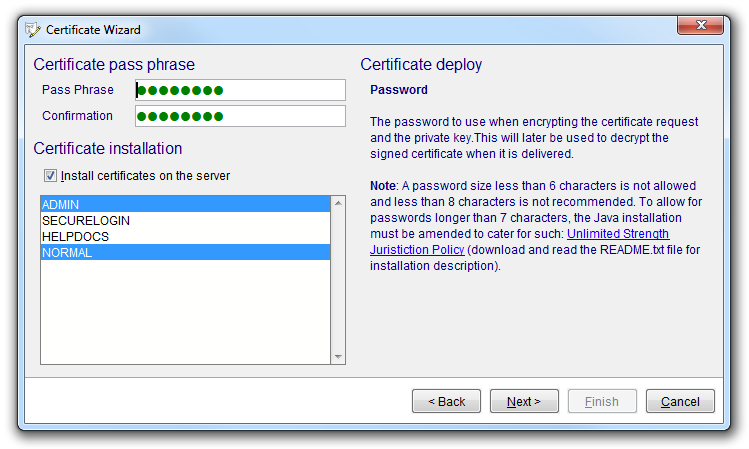
Each certificate is then signed with a selected password. Optionally, the certificates can be installed for one or more access profiles. These profiles are used to specify how resources are accessed and protected on the NetPhantom server. If selected, the set of access profiles will be populated with all the client certificates created by the wizard. After restart of the server or the SSL port(s), this will allow access for all clients holding the relevant certificates. The client certificates are stored in the SSL repository on the server to be physically distributed to trusted clients.